For internet security and safer browsing

FireFox
FireFox is always recommended over Internet explorer. FireFox isn’t nearly as buggy and is open source. With Firefox we recommend Ghostry and Https Everywhere plugins as a standard. Ghostry also has a phone app web browser that is pretty good.
VPN (Our Security Rating B)
A VPN or Virtual Private Network allows a user to connect to the internet through a third party. Your connection to the third party is encrypted and your ISP (Internet Service Provider) will only see a connection only to the third party. Your internet is not encrypted after leaving the third party unless the website uses https. Most commercial VPN’s keep logs of where you visit and will bow down to law enforcement. We recommend Riseup’s VPN. If you find there setup complex then you can purchase a VPN for about $40 a year. Make sure you pick a reputable company that doesn’t keep logs. We also recommend Private Internet Access but there are others out there. Remember when using a VPN you are putting all of your trust in someone else not to expose what you are up to.
https://www.privateinternetaccess.com/
Protonmail.com (Our Security Rating A)
Protonmail offers a free email address and even has an app available. They are mostly opensource at this point and working on being fully. People like them even though they currently do not work with programs like thunderbird or Outlook because they have a very strong encryption and privacy . When you email someone else also using Protonmail the email doesn’t go out on the internet it stays in their network and is encrypted end to end. This is a new breaking tech that allows a seamless encryption over clunky encryption programs that require a little learning.
https://mail.protonmail.com
Signal (Our Security Rating B)
A simple phone app that will encrypt your messages to other Signal users. This app can replace your messenger and handle all of your texts. It is easy to use and has a timed deletion that you can set if you choose.
Tresorit (Our Security Rating A)
A fairly simple cloud service that specializes in security and is free for up to 2GB of storage. It can sync with your laptop, desktop and even has a phone app. They tout not to lose your password as they can not recover anything for you because it’s encrypted and they don’t have access.
https://tresorit.com/
KeePass (Our Security Rating A)
This is a fairly simple opensource program to keep all of your passwords protected and secure. You can use this in a windows environment and they have an app also. It has some advanced security features available making it nice. It’s important to have a password program like this because you should not be able to remember 99% of your passwords because they are way too complex. You’ll need to remember this one though to get into your passwords but don’t skimp out on making it tough.
http://keepass.info/
Tor (Our Security Rating A+)
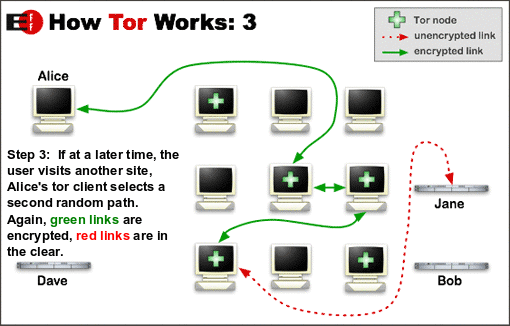
If you want something a bit more private, then there is Tor and the Tor Project. Tor acts like a multilayered VPN with more levels of encryption. Instead of relying on one entity to secure your privacy, you are directed through three; two of which do not know who you are and the other not knowing what you are sending or receiving.
Tor encrypts your connection to the internet. The first person in the network – Party (A) – receives your request but cannot read it because your connection is encrypted (under several layers like an onion). Party (A) can see your IP address but doesn’t know what site you are visiting or any information you are inputting. Party (A) then sends the “information packet” to the next person in the chain – Party (B). Party (B) has no idea who you are because they do not receive your IP address. Party (B) is instructed to give the anonymous and encrypted information packet to Party (C). Party (C) is the “Exit Node” to the internet. Party (C) does not know who you are nor do they know the identity of Party (A). Party (C) takes the information packet from Party (B) and removes the final layer of encryption. Party (C) then sends the anonymous information openly across the internet.
Here is a summary of Tor’s network:
Your Computer –> Your ISP sees your connection to Party (A) [encrypted]
Party A – Knows who and where you are but not what you are sending or receiving.
Party B – Doesn’t know who you are, where or what it is sending or receiving for you.
Party C – Doesn’t know you or Party A or your locations but as the final “Exit Node” they know what you are sending and receiving across the internet.
From here your information is open on the internet as it travels around and connects to the website. The website you are visiting doesn’t know your identity (unless you tell them i.e. login). The website only sees Party (C) visiting their site.
In addition to Tor, we recommend a FireFox plugin called Https Everywhere. This plugin was put together and made possible by the respected activist group Electronic Frontier Foundation (EFF). If a website you are visiting uses https encryption, the plugin finds the encrypted pages so you will connect to https everytime. Sometimes these pages are hard to find or intentionally hidden on a website, which is one of the reasons the Https plugin is important. With Https Everywhere you are fully encrypted (end to end) and the plugin can be used with Tor in the Tor Browser Bundle (plugin included). End to end encryption means that Party (C) the “Exit Node”, anyone snooping in between the connections, and/or the website you are visiting will only see an encrypted message.
https://www.torproject.org/
https://www.torproject.org/projects/torbrowser.html.en
Tails (Our Security Rating A++)
If you like Tor, you may like Tails. Tails is an “amnesic” program which works independently of a computer’s operating system. Tails does not use the computer’s hard drive, which allows a person to use a computer without leaving a trace of any sensitive documents, browsing history and eliminates the possibility of data recovery after shut down. For more information visit:
PGP (Our Security Rating A+)
PGP or Pretty Good Privacy is an encryption program used primarily for email and whole disk encryption. Commercially, many companies use PGP to protect trademark secrets. PGP costs around $200 for a life time license. It is our understanding that some cracked PGP versions have been found on the internet. PGP 6.5.8 can sometimes be found for free and used for non-commercial purposes. It is a very old and light version that cannot handle some large but standard encryption keys used today. PGP encryption has never been cracked even in activist court cases.
https://www.symantec.com/encryption
GNUPG – is the free open source version of PGP and is trusted by many activists. GnuPG keys work with PGP keys and vice versa.
PGP and GnuPG may take some getting used to but should be used for encrypting ALL email. PGP offers a whole disk encryption for your computer also.
Security is never fool proof and usually they wont bother trying to crack your encryption. Instead they use work arounds like keyloggers. Do your best and make it a standard. Keep passwords very strong and make sure everything is encrypted. Change your passwords from time to time and keep your security updated. Use of Firewalls like Comodo and anti-virus like Avast are always good options (keep them updated). If you want the best there currently is then learn to use Tails.